IC Security Deficiency
Absence of law.
Attempts at improving cyber legislation have been deficient. The absence of legislation causes issues for CIKR. The lack of production led to an executive order issued by the Obama Administration (Godreau, 2013). In February of 2013, the President (Executive Order [EO] 13636, 2013) signed EO 13636, the Preliminary Cybersecurity Framework. This is a basis for cybersecurity infrastructure. It does not mandate how entities are required to secure their systems. Due to the absence of law, executives will view productivity over security because the cost of mitigation appears more than any perceived impact of cyberattack (Langner & Pederson, 2013). The EO explains the legislation as a public review and comment process conducted by the Cybersecurity Framework Director (EO 13636, 2013). Business governance steers the conduct of executives on issues of national security; cost is justified in terms of profit. Costs for security would be budgeted if fines or sanctions were the result. The problems created by networked infrastructures are complex. Without law to dictate how to handle security in these environments, achieving forums for investigation and discussion will stall between government and industry (Godreau, 2013). Congressional cooperation on the issue is minimal. The last three Congresses proposed over one hundred bills though none became law (Fischer, 2013). Regulation is not the end resolution. Cybersecurity issues cannot be resolved with regulation alone (Godreau, 2013). The federal government defined 18 sectors within CIKR owned primarily by the private sector that require legislative action for increased security (Fischer, 2013). Bureaucracy prevents the increase. Extensive agreement exists that supplementary actions need to handle risks to CI caused by deficiencies in cybersecurity, however substantial disparity remains about any required additional federal regulation (Fischer, 2013, p. 13). The inability of the government to enact legislation remands the problem to security practitioners. Several challenges exist that introduce tough questions for cybersecurity whereby a need is present to revise the National Infrastructure Protection Plan (NIPP). Questions related to responsibility, accountability, obligation, performance monitoring, provision of resources, disaster liability, economic loss compensation, and societal responsibilities for increased security are not answerable by the current NIPP revision (Auerswald, et al., 2006). Practitioners use risk assessment for mitigation. Entities want manageable solutions to reduce threats (Honeywell, 2014). Risk assessment applications are helpful; however, they do not absolve the problem. Organizations that run ICS’s admit to insufficient staffing for management of key elements (Honeywell, 2014). Though the federal government has indicated that these networks are vital, inaction leaves them self-reliant and susceptible to attack.
Defensive posture.
Part of the problem stems from the rapid evolution of technology. Army General Keith Alexander mentions the need to protect networks including critical infrastructures (Roulo, 2014, p. 6). Another concern is NSA surveillance and its creation of public scrutiny. The division in agreement between the nation and its people on what is legal behavior in cyberspace slows progress (Roulo, 2014). The U.S. GAO implicates management issues as well that ultimately affect defense (US Government Accountability Office, 2011). Finding common ground is imperative to building better security concepts. One other resounding issue for cybersecurity in general concerns a tunnel-vision approach. The intention depends on static processes and or tools meant to accomplish defensive postures for these architectures. In short, traditional defense is responsible for failure, due largely to the inability to provide traditional defense (Lee R. M., 2015). Cybersecurity requires processes that include dynamic attributes. Unfortunately, mainstream defensive techniques do not generally retain such properties. The ability to scrutinize and analyze a network at a granular level is not possible with just passive techniques (Lee R. M., 2015).
Active defense.
The cybersecurity timeline contains valuable lessons learned that should be useful as hindsight. These findings show how important it is to apply security metrics through dynamic cyclic processes rather than relying on static or physical applications alone. Application of cybersecurity becomes more resilient when Tactics, Tools, and Procedure (TTP) couples with constant monitoring efforts. Monitoring efforts determine information about adversaries and their methods whereas simply using static tools to secure the network will eliminate this prospect (Bejtlich, 2014). Active defense efforts are those such as the Active Cyber Defense Cycle (ACDC) proposed by Robert M. Lee. This dynamic cyclic process includes Asset Identification and Network Security Monitoring (NSM), Incident Response (IR), Threat Environment Manipulation (TEM) and Threat Intelligence Consumption (TIC). Figure 3 is an example of ACDC.
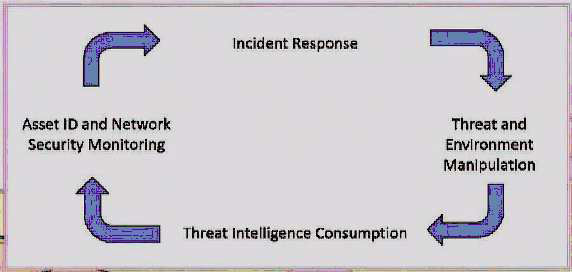
Figure 3. Active Cyber Defense Cycle by CYB 649: Advanced Topic in Cyber Operations. (Lee, R.M., 2015).
Attack surface.
Losses due to cyberattacks against IC’s are a function of achievable action and expected frequency (NSA, 2010). Attackers may not even require cyberweapons to infiltrate ICS’s. A technique known as “spear phishing” uses deception to target specific individuals to achieve access to the target (Mello, 2013a). Surplus resellers present additional vulnerabilities by remarketing unsanitized equipment pulled from factory floors and containing propietary and or authentication information in the equipment’s memory (ICS-CERT, 2013). Nefarious attackers could easily use this equipment to spearhead exploits. Research performed via Shodan software revealed 95,000 devices that speak Modbus are reachable on the Internet (Higgins, 2013). The vulnerabilities of SCADA networks has risen more than 500% between 2010 and 2012 (Frei, 2013). The first half of 2013 showed 200 incidents requiring response by ICS-CERT across all sectors of CIKR as depicted in Figure 4 (ICS-CERT, 2013).

Figure 4. ICS-CERT response analysis for 1st half of 2013 by ICS-CERT Monitor (ICS-CERT, 2013).
The prospective threat sources expand the attack surface. Insiders, terrorists, activists, cybercriminals, nation-state sponsored attackers, and competitors can target ICS’s (NSA, 2010). Note that these threats include both internal and external sources. Most of society uses computers though many of them have minimal technical skills or cyber awareness. Consider that some attacks may not be intentional and the level rises again. The Systems and Network Analysis Center for the NSA detailed a scenario about removable media spreading malware onto an ICS whereby the original plan for the infection was for another system (NSA, 2010). Building a defensive position for an ICS is difficult. To begin a protective application on a standard network it must be mapped (Leverett, 2011). In respect of an ICS, commands used to map a network may create a hazard. For example, in one incident a plant experienced a loss of $50,000 in integrated circuit wafers when a ping sweep caused the plant to hang (Stouffer, Falco, & Kent, 2006). Control system engineers will seek to keep these actions from happening though malicious players follow no restrictions (Leverett, 2011). With simple scans being so detrimental, ICS vulnerability is high and they have difficulty-achieving defense. The problem of implementing security measures reveals more of the attack surface.
Supervisory control and data acquisition scenarios.
The vulnerabilities of SCADA are apparent within the present profile of cybersecurity. Modernized society is dependent on SCADA systems. SCADA systems influence the well-being of citizens and they remain targets for terrorism (Udassin, 2008). Another aspect to consider is the profile of the entity responsible for attacks on ICN’s. Attacks presented by the proposed research derive from no ordinary hacker; well-funded and well-equipped control experts execute cyber assaults (Udassin, 2008). Illustrated in Appendix A is a list of twenty-nine events occurring between 1997 and 2009 related to SCADA hacks. Some of these events are purposed demonstrations; all are indicative of vulnerability inside ICS’s. SCADA has three attack vectors- field attacks, corporate attacks, and physical attacks. In consideration of such environments and their previously mentioned states, vulnerability increases substantially. Attacks on ICS’s occur from the field, from corporate systems, and from physical attacks (Udassin, 2008). The proposed research emphasizes that virtual attacks multiply the cyber-attack vector rather than the physical one. Examining a physical field attack scenario emphasizes security issues of an ICN. Regulation of field devices takes place at the central hub where the functions of an ICS’s control servers reside (Udassin, 2008). The attribute of the field environment exhibits the initial issue. As in any line of defense, a broader defensive front weakens resistance. Field workstations in unmanned areas allow infiltration into SCADA networks, making them challenging to secure and dependent upon physical security parameters such as fences and locks (Udassin, 2008). In very little time, a research team managed to determine vulnerability and execute an attack on a petroleum distribution entity in such a field location. Using a demo of the software running on the target system and the W32RTR.EXE process, arbitrary code exploited a heap based buffer overflow weakness. Buffer overflows dominate remote network vulnerabilities due to their provision of code injection and execution abilities (Cowan, Wagle, Pu, Beattie, & Walpole, 2000, p.1). The weakness uses a designer payload packet to exploit the system providing a remote shell with elevated privilege (Udassin, 2008). This supports the information released by Italian researcher Luigi Auriemma who recorded thirty-four vulnerabilities associated with ICS’s specifically related to heap overflows (Peterson, 2011). Next is a review of an attack on a SCADA corporate network. Udassin (2008) indicates why corporate networks are easier targets in the following
1) They interface with the Internet;
2) Users in this environment are less educated about information security;
3) There are external machines hosted by the network.
The attack’s objective is the firewall between the corporate network and the SCADA network. The research team performed this attack using an out-of-the-box Proficy installation in conjunction with the Java remote method invocation protocol; this is equired for a connection between the Proficy web application and the user’s browser (Udassin, 2008). The attack then uses intelligence-gathering tools to establish a connection. An incorporated network sniffer aids the attack by disclosing a login packet where a clear-text username and encrypted data using Base 64 are exposed (Udassin, 2008). The password was located by using the intelligence in that packet which presented the encrypted Base 64 data. Another packet generated by the targeted user provided details. Through packet modification, file creation accomplished and gained the server’s acceptance; an Active Server Page (ASP) file compilation opens a remote shell backdoor and bridge to the SCADA network (Udassin, 2008). The legacy code still used by SCADA systems ensures vulnerabilities are vaible for future exploit (Peterson, 2011).
XP machines not retired.
A large percentage of the population of computers still uses Windows XP. Microsoft ended support of XP on April 8, 2014 (BCS, 2013). Those machines running Windows XP in ICS’s are susceptible to attacks. Approximately eighty percent of Britain’s National Health Service is still using Windows XP (BCS, 2013). Computers still rely on Windows XP platforms for programming and monitoring of IC’s currently (Zatarain, A. M., 2014). The changeover has been slow. Mission critical machines used for utilities are apart of this group (Shook, 2014). Older machines become obsolete because newer platforms require updated hardware (Clarke, 2013). Enterprise systems still using the old platform will have to be overhauled. Other areas of CIKR are migrating platforms but they are incomplete (Zatarain A. M., 2014). One instance of the populace still widely using Windows XP is China. China is lagging behind in the migration to newer operating systems (OS). Part of the resistance is attributed to ideals that mitigation causes more potential for security threats (Ramzy, 2014). The analysis firm StatCounter noted 49 percent of Chinese computers still use this Windows OS (Ramzy, 2014). Several reports of the five year old Conficker worm still affecting this region validates that many systems are using this OS (F-Secure, 2014). Key problems are associated with Windowx XP. This OS is difficult to repair once comprimised. Two serious threats to Windows XP machines, web-based attacks and Java-based attacks, indicate prevention is advisable over seeking a cure (F-Secure, 2014). Another difficulty presents economic ramifications. “According to Bloomberg BusinessWeek, as many as 90% of all ATM machines are still running Windows XP” (F-Secure, 2014, p. 16). XP machines face a two-thirds increase in rate of infection after the final security patch (Keizer, 2014). Migrating the computers running this OS version will take time beyond the cut-off date. The precentages translate to approximately 488 million systems operating on XP as of February 2014 (Keizer, 2014). One of the obstacles to upgrading is caused by systems built before today’s 32 or 64 bit platforms. Windows 7 and later minimum requirements, listed below in Figure 5, create the obstacle.

Figure 5. Windows 7 Requirements from How to Upgrade (CCS, 2014).
Upgrades require vendor compatability as well. Industrial organizations often depend on systems with code developed before Windows 7 (CCS, 2014). This means much of the supporting vendor software remain dependent on the older OS. Vendors without compatible versions for the new OS will require other software upgrades in addition to the operating platform (CCS, 2014).
Infrastructure catastrophes.
Aims to reduce catastrophe use lessons learned through practical exercises or incidental occurrence as teaching points. The lessons learned inevitably fail to demonstrate the technological shortcomings that are present within society. Historical examples ranged from maritime transport, aviation, deep-water drilling, and space exploration (Cavnar, 2010, pp. 49-53). Misguided Titanic engineers ignored their practice and followed executives seeking appearance and accessibility. Though design, structure, navigation, communication, and safety advanced afterward, it came at the cost of over 1500 people (Cavnar, 2010, p. 49). Another case is the Deepwater Horizon blowout in April 2010. Maintenance errors, coupled with miscalculations in the well’s design and blowout prevention system’s capability, allowed a manageable problem to evolve into an environmental disaster (Zatarain, 2015). Though these incidents did not stem from cyber related attacks, they epresent the severity of the widespread impact resulting from infrastructure disasters. The practice of overlooking security in its relation to safety is a common occurrence that can result in equally disastrous events. The explosion of the Siberian pipeline in 1982 is comparable to the scale of a nuclear detonation (The Archive, 2013). This is an example of a catastrophe relatable to an attack on a SCADA facility. Some viewpoints consider this event as the first known act of cyber warfare. During the era of the cold war, the Soviet Union had established an intelligence espionage operation. A Soviet defector exposed the espionage operation. The counter-intelligence that followed is said to have included fallible code for IC’s which was incorporated by the Soviets in the Siberian pipeline project (The Archive, 2013). Although the explosion claimed no casualties, it caused ramifications for the Soviet economy (Loney, 2004). In Arizona, the Roosevelt Dam incident in the 1990’s, concerning a young man who compromised its ICS by gaining control over its SCADA servers, is another instance (NATO Science for Peace and Security Series, 2008). A disaster caused by a SCADA cyber event with the Roosevelt damn could inundate Phoenix, Arizona with 1.6 million acre-feet of water. The United States’ fifth largest city would have only a few hours to evacuate 3.7 million people (Bommersbach, 2006). As another example, reflect on an assault that overcomes the telecommunication system governing airline transportation. A1997 incident linking a juvenile with the Worchester, Massachusetts Airport represents an event where interrupted phone service for safety and security resources demonstrates a significant potential for calamity (NATO Science for Peace and Security Series, 2008). An airport could face disaster when response capabilities and operational provisions are unavailable. A staged event in November of 2013 known as GridEx II indicated the damages that result from a cyber-assault on electrical infrastructure (Wald, 2013). The resulting details serve as validation that ICSs are vulnerable, and that the nation’s CIKR are at risk. Results from the drill indicated a loss of power for tens of millions, hundreds of damaged or destroyed transmission lines and transformers, and an ICN infected with malware still running processes (Wald, 2013).
Potential impact.
Hypothetical constructs and practical scenarios are the only result of the deficiencies correlated with SCADA and ICS’s. Moreover, although Government has worked to prepare for a cyber-incident, the information presented by simulated damages shows the Government’s attempts to prepare for cyber incidents are unsuccessful. A singular attack could equate to economic and physical losses. This raises some questions. Multiple events happening simultaneously as they unfolded on 9/11 overwhelmed emergency resources. The length of time required for recovery for 9/11 has exceeded a decade. The nation is not prepared for secondary conditions resulting from a multi-incident cyberattack similar to 9/11. Defense Secretary Leon Panetta stated that a cyber-assault equivocal to 9/11 could be destructive and leave the nation incapacitated (Kerr, 2013). Security experts specify the time since 9/11 is a waste. Opponents argue desired improvements for funding is the reason behind such statements. The cybersecurity community is aware of the catch-up required (Clayton, 2014). The legislation and needed workforce mirrors the gap between security and SCADA assaults. Now referenced as the “lost decade,” the progress is minimal and a number of ICS’s are accessible on the Internet, unprotected from hackers, and deficient in security (Clayton, 2014). Voluntary cooperation is necessary for mitigating incidents. Acquiring incentive by developing sound security practices within the private sector should be the focus (U.S. DHS, 2011). DHS recognizes specific categories of impact to quantify loss. Categories of impact for consequence are human, economic, public confidence, and government functionality (U.S. DHS, 2011). A well-positioned attack can affect all these categories. Accomplishing an attack by targeting the concentration of people on an urban public transport system is achievable by maximizing an attack with minimal resources (Al-Askandrani et al., 2013). The perspective on the interconnection and reliance between different sectors of CIKR is underestimated. The interdependency of critical infrastructure becomes more complex daily and the functions of these utilities are a necessity for societal continuance (Huler, 2010, p. 216). Figure 6 presents this interconnection.

Figure 6. SCADA interdependencies by Identifying, Understanding, and Analyzing Critical Infrastructure Interdependencies
(Renaldi et al., 2001).
“They are all complex collections of interacting components in which change often occurs as a result of learning processes; that is, they are complex adaptive systems” (Renaldi, Perenboom, & Kelly, 2001, p.13). Attacks on interdependent infrastructure can cause cascading effects. “What happens to one infrastructure can directly and indirectly affect other infrastructures, impact large geographic regions, and send ripples throughout the national and global economy” (Renaldi et al., 2001, p.11).

