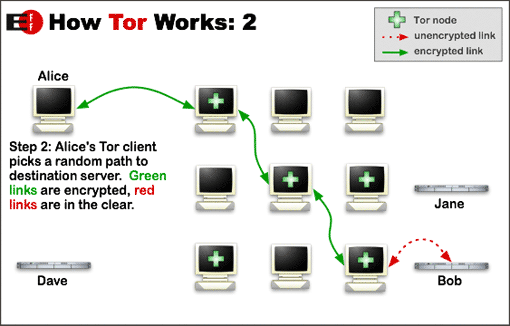
Criminal Activity on Tor
When standard communications traverse the Internet, they do so in form of TCP/IP packets. These packets are like envelopes that are stamped with the address of the intended recipient and the return address of the original sender . If a third party wanted to know the contents of a postal letter, they could intercept the envelope while it was in route open it, and read the message inside. The same is true for unencrypted TCP/IP packets. A third party can collect packets as they traverse the Internet, reassemble them, and reveal a message’s contents. And, just as in the example with the letter, a third party would also be able to see who is communicating with whom and record information on the nature of their communications such as how often they communicated, when they communicated, and the length of the communications
Assessing the Availability of Anonimizing Technologies
The Practice and Policy of Global Internet Filtering, author and political science professor Robert Deibert examined worldwide patterns of 23 Internet censorship and surveillance. Deibert’s findings drew extensively from data recorded during a four-year investigation conducted by the anti-Internet-censorship organization the OpenNet Initiative (ONI). From 2003 to 2006 the ONI team systematically assessed Internet accessibility from within 41 countries and concluded there was empirical “…evidence of technical filtering in twenty six (countries)” . Based on this information, Deibert concluded the Internet’s architecture was fundamentally shifting toward a closed information environment subject to exploitation and manipulation by nation-state actors. While the Internet had its roots in a single open global network meant to facilitate the sharing of ideas and research, a trend had emerged where access to the Internet was being denied along geographic lines in order to protect political interests. Deibert faulted authoritarian states that sought to control the public’s perception of social and political issues as the primary perpetrators of Internet censorship, and he made the prediction that additional nations would justify implementing some kind of Internet filtering as a defensive measure in the years to come
Chinese-style (first generation) filtering
In Chinese-style (first generation) filtering, lists of Internet Protocol (IP)
addresses, keywords, and/or domains are programmed into routers or software packages that are situated at key Internet choke points, typically at international gateways or among major Internet service providers .This approach blocks specific traffic and is simple and effective, but it can quickly be bypassed by using virtual private networking (VPN) connections or proxy servers. With these systems a user connects to a machine outside the filtered network and creates a secured, dedicated, and encrypted connection back to the original machine. Once the connection is established, the system inside the filtered network uses the machine outside the filtered network to relay requests on its behalf.
The filtered network’s gateway cannot read the information because it is encrypted, and therefore, the traffic is allowed to pass. State-sanctioned countermeasures employed to prevent this from happening add the IP address of known VPN and proxy relays to the list of blocked addresses, or they simply do not allow any encrypted traffic through international gateways .Second-generation controls create a legal and normative environment and technical capabilities that enable actors to deny access to information resources as and when needed, while reducing the possibility of blowback or discovery. These controls have an overt and covert track. The overt track aims to legalize content controls by specializing the conditions under which they can be denied… The covert track establishes the procedures and technical capabilities that allow content controls to be applied ‘just in time’… (e.g. during elections or public demonstrations)