Vulnerabilities and Threats – Security Concerns
A threat is anything that can cause an interruption to network operation or system’s functionalities and can jeopardize its availability. There are different categories of threats including natural threats like floods, earthquakes, storms and unintentional accident type of threats. Also there are intentional threats that are caused by malicious intent. Each type of the threats can be catastrophic to a network. A vulnerability on the other hand is an open hole or fault susceptible to a threat attributed to intrinsic weakness in the design, configuration, or implementation of a network or system. Most vulnerabilities can usually be traced back to one of three major sources; poor design, poor implementation or poor management.
Many vulnerabilities have been identified in smart grids employing SCADA control systems operating on different protocols. According to DHS ICS-CERT monitor report, cyber-attacks has increased from 9 in 2009 to 245 in 2014 and the reported number of incidents affecting various critical infrastructure is tabulated in Table 2.2, but the actual number could be much higher than what is indicated in the table since a lot of organization fears from negative publicity:
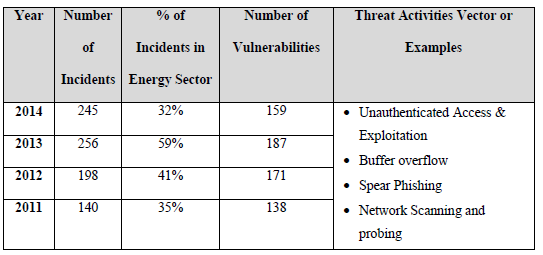
TABLE 2 NUMBER OF INCIDENTS AND VULNERABILITIES

TABLE 2 NUMBER OF INCIDENTS AND VULNERABILITIES
In 2014, there were 159 known vulnerabilities in control system with the majority exist in the Energy Sector.
Attack and Penetration strategy
Attackers usually follow certain strategy or methodology to perform system attacks against the target network or host similar to the techniques that is being used by penetration testers. It is based on a sequential multi-stages attack (figure 7). The stages involved in performing the attack are listed as follows:
1. Reconnaissance or data gathering stage
2. Scanning for potential target(s) and possible vulnerabilities
3. Exploiting the vulnerability discovered in step 2
4. Accessing the compromised host through logical connection
Each stage will require planning and preparation in addition to acquiring specific security tools that might be needed to perform the stage. In general, different tools will be required in each of the stages mentioned above and most of the tools are available over the internet and sometimes special ones can be coded and customized to serve a specific purpose. The methodology can
include searching for vulnerabilities, performing sequential attacks, building an attack graph and weak point’s identification.

Figure 7 Penetration Strategy – Sequential Attacks
Critical Infrastructure Security Concerns
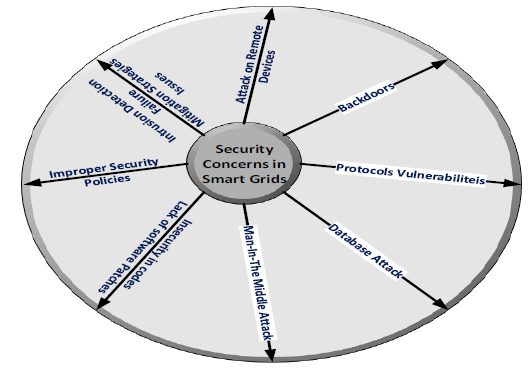
Critical cybersecurity concerns that need to be addressed in critical infrastructure are so many and the list is growing. Figure 8, shows some of the more pressing security concerns including backdoors, protocol vulnerabilities, database attack, man-in-the-middles (MITM), unsecured code, lack of security policies, intrusion detection failure, attack on remote devices and many others.

Figure 8 Cyber Attacks – Security Concern
Risk Management
Risk in is defined as the exposure to danger and risk management is the process of identifying vulnerabilities to organization’s infrastructure and assets in order to prepare mitigation strategies to eliminate or reduce the risk. Therefore, risk management starts with risk identification to identify, classify and prioritize threats, then risk assessment to identify vulnerabilities and finally establishing mitigation strategies to reduce or control the risk.
Risk is a function of three important variables; vulnerability, threat and impact and the risk will increase if any of those variables increases. Therefore, in order to minimize the risk we need to know our threats in order to provide control measures to reduce the probability of having a vulnerability as a result of the threat. Figure 9 below, shows our framework in addressing the risk management starting with vulnerability assessment and followed by threat and impact analysis.

Figure 9 Risk Management
According to the National-Infrastructure-Protection-Plan (NIPP) and the Energy Sector- Specific Plan (ESSP) , both addresses the security and resilience in critical infrastructure through collaboration between private, non-profit organizations and other governmental sectors. Objectives are related to prioritizing goals, mitigating risks, measuring progress and adapting to environmental changes. Physical, cyber and human are the three elements of critical infrastructure risk management framework and the framework is based on five phases as follows:
1. Set Goals and Objective’s
2. Identify Infrastructure
3. Assess and Analyze Risks
4. Implement Risk Management Activities
5. Measure Effectiveness