Potential Infrastructure Breach Points
Airlines have public-facing websites that allow customers to book their reservations. The web servers, if not correctly updated and patched, can leave holes for a cyber-attack. Karen A. Forcht, professor in the Department of Information and Decision Sciences, and Richard E. Fore, have authored general articles in security and the Internet. In 1995, Forcht and Fore wrote that Distributed Denial of Service (DDoS) attacks could render a network or computer resources unavailable for the intended audience to use. As no single entity has authority over the Internet, no policies exist to secure the traffic over the Internet (Forcht & Fore 1995). nfrastructure breach points include, but are not limited to, devices, infected emails, network attacks, andelectronic communication from disguised entities.
USB Storage Device
Neil J. Rubenking a technical editor for PC Magazine authored “An Evil USB Drive Could Take Over Your PC Undetectably.” In his article, Rubenking stated that users store and share files with a USB storage device but do not scan the USB device to remove the malware, if any. When the user inserts a USB storage device into a computer, the computer reads and then auto-runs executable files. Dangerous malware in the USB storage device will execute and infect the computer and spread (Rubenking, 2014). Antony Savvas, a technology journalist and contributor for ComputerworldUK.com and author of enterprise and consumer IT, explained that once the malware has started, it would begin to replicate and reinfect the computer at every reboot (Savvas, 2010).
Email, is a low-cost medium that hackers can use to send spam. Spam emails are emails sent to a large number of recipients that resemble those sent from legitimate companies. Email can contain unknown threats if the user opens an attachment or if the user clicks on links inside the email. A few ways to prevent email malware infection at work are not opening any unsolicited email, saving the attachment instead of opening it, running a virus scan prior to opening the attachment, marking items as junk mail, and not using work email addresses (Targeted News Service, 2011).
Phishing
Phishing not only comes in email form, but it also comes in the form of fax and letters via post mail. Consumers received a letter in the mail stating they have won airline tickets. The criminals embedded the printed letters with real airline logos and included what appears to be the office address of the airline’s headquarters. The criminals also included the URL link to the airline’s legitimate website. Further, the letter congratulated the consumers and included a phone number to call and redeem the tickets (US Fed New Service, Including US State News, 2012).
Eavesdropping
Eavesdropping occurs by using a radio that can operate at 1090 MHz in combination with an open source ADS-B receiver. A terrorist can use eavesdropping to their
advantage as they can tap into an aircraft communication. The terrorist is easily able to locate the exact location of the aircraft and cause a flight to deviate by injecting false information to flight crews. Terrorist perform this by using simple radio frequencies allowing the terrorist to bring down an aircraft and potentially causing loss of life. Eavesdropping alone is harmless; however, it is the groundwork for a more refined attack. Lack of full encryption not only prevents discovering eavesdropping, but it also makes it impossible (Barreto & Kacem, Costa, & Wijesekera, 2014).
Man in the middle
Causing confusion to the air traffic control is another goal of a hacker. Man in the middle gives the hacker using the eavesdropping method mentioned above the ability to alter captured data packets transmitted by the aircraft. Once the hacker has altered the data pack, the hacker sends the altered data to air traffic control, providing false information and creating mass confusion (Barreto et al., 2014).
Denial of Service
Similar to the man in the middle or eavesdropping techniques, denial of service can cause havoc. Hackers use denial of service to feed mass amount of fake flights into air traffic control system. The mass amounts of fake flights would cause controllers to be unable to determine which flights are real and which are not effectively rendering objective communication to live flights useless. Essentially, hackers use denial of service to cause a diversion such as loss of communications with aircraft in order to mask their real objective (Barreto et al., 2014).
DDoS
Cyber-attackers use DDoS attacks for reasons such as extortion, political sabotage, and even cyber terrorism. Margaret Rouse, writer for TechTarget, stated that hackers use servers to launch DDoS attacks by installing code into servers and compromising them. The servers then allow attackers to launch the DDoS to the victim’s site. A type of DDoS attack called network-centric is another method used by hackers. This type of attack overloads services and applications by inundating them with packets and causing degradation of service (Rouse, 2013). Robert McGarvey, a technology reporter for various publications, authored articles on payments and banking. In 2013, McGarvey reported that a political driven DDoS attack took place against the Patelco Credit Union in Pleasanton, California and University Federal Credit Union in Austin, Texas (McGarvey, 2014). Russian airline Aeroflot is an example of a politically driven cyber-attack. In 2010, Aeroflot experienced a DDoS attack that caused their online ticketing system to be unavailable from July 15th to the 24th. Pavel Vrublevsky, a prominent Russian computer programmer, entrepreneur, and the former CEO of ChronoPay, a credit card payment processing company, instigated this attack. A court convicted Vrublevsky after he hired two hackers, Igor and Dmitry Artimovich, to carry out a cyber-attack against the Russian Flagship Air Carrier, Aeroflot.
Officials believed the attack prompted the airline to end its business contract with Assist, a competing e-payment and credit card processing business (Russian Legal Information Agency [RAPSI], 2013). A similar attack occurred in 2015 that caused the Malaysia Airlines Company website to experience an outage. Customers attempting to access Malaysia Airlines’ website and planning to make travel bookings saw instead, another page. The website displayed an image imitating the common Internet browser error 404 page not found message, but instead the website displayed “404 – Plane Not Found.” A group, Lizard Squad, performed the hack, although the French news agency Agence France-Presse provided no motivation. Additionally, according to media reports, in other geographical regions containing versions of the airline’s website, the hacked website displayed the wording “ISIS will prevail” (Agence France-Presse, 2015). Following the attack, Paul Armstrong, editor for CNN reported that Malaysia Airlines issued a post on their Facebook account, notifying customers that the data breach had no information containing passenger data. The post also stated that the hackers redirected only the Domain Name System (DNS). Malaysia Airlines was working to restore their website with their service provider and expected to be operational within 22 hours. In the meantime, Malaysia Airlines redirected users to an alternative link for their booking service (Armstrong, 2015). Figure 3 shows the hacked website seen by customers.
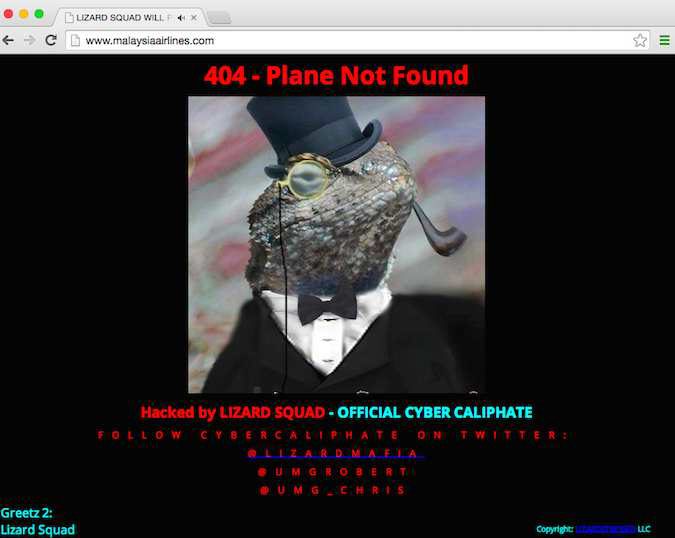
Figure 3. Malaysia Airlines website hacked by Islamic State jihadists known as Lizard Squad (AFP, 2015 “Hackers Target
Malaysia Airlines,” para. 1).
Protocols
Protocols are rules that control communication between computers on a network. Each protocol is required to ensure that communication is available between all types of computer hardware and applications (Florida Center for Instructional Technology, 2013). Examples of protocols are: Transmission Control Protocol/Internet Protocol (TCP/IP), Hypertext Transfer Protocol (HTTP), Transport Layer Security (TLS), and Secure Sockets Layer (SSL) (Florida Center for Instructional Technology, 2013).
TCP/IP
TCP/IP handles managing communications between the application layer and transport layer on a network (Forcht & Fore, 1995). TCP/IP spoofing is a method attackers use to imitate a computer that is known by the network. Computers on a corporate network have their own Internet Protocol (IP) address that identifies the computer. An attacker can use spoofing to gain access to not only that computer but also other devices on the network such as network servers and other computers (Forcht & Fore, 1995).
HTTP
The HTTP protocol is an Internet-based protocol that networks use in conjunction with TCP for sending and receiving web pages. Cyber-attackers intercept the HTTP request and redirect users to a phony website. Cyber-attackers use phishing scams via email that have a link to a fake website (Forcht & Fore, 1995). In 2012, Paul McNamara, a news editor for Network World, received an email from US Airways containing a confirmation code for a trip. The email contained information not only referencing the confirmation code but also displayed a check-in link for a flight (2012). The link provided by the phishing email directed unsuspecting customers to a fake website maintained by the hackers that required the user to enter personal information (McNamara, 2012).
TLS and SSL
TLS and SSL work in conjunction with each other by providing an extra layer of security over the Internet when accessing websites, email, and other applications. The Heartbleed bug found in 2014 exposed a vulnerability in a version of OpenSSL, an open source implementation of SSL and TLS protocols. Heartbleed allowed sessions to remain open between servers and clients. This open session allowed for the capture of user identification (ID) accounts, passwords and other sensitive information (CODENOMICON, 2014). In 2015, Robert Hackett, a writer for Fortune author of various articles in data breaches, explained that not all corporations have fully corrected the vulnerability with the Heartbleed bug (Hackett, 2015).
Viruses
One of the most common and widely used methods for attack is malware that, once executed, replicates itself, exposes vulnerable corporate networks, and renders back doors for cyber-attackers to use. Spam email, or files downloaded unknowingly from a website, might contain a variety of viruses (Microsoft, 2014). Tom Nevin, contributing author for African Business has written articles related to IT security. In 2001, Nevin explained that a computer virus could stay dormant for years until some certain mechanism activates it or activated by the creator (Nevin, 2001). Laura Gordon-Murnane, a freelance writer and information professional has authored
articles in security. In 1999, Gordon-Murnane explained, viruses’ purpose and malignity are as diverse as the number of viruses out on the Internet. Some are created to be a nuisance. Others are created to force a customer to pay for a so-called service or program required to disable the virus. During this time, a service is created by the author of the original virus. Other more potent viruses are created to cause havoc on the system and expose vital and valuable personal data (Gordon-Murnane, 1999).
Viruses range from simple, and almost harmless, to very complex virus programs created to wreak havoc on systems. The viruses are dangerous and built with a specifically designed purpose. In 2012, Sharon Weinberger, a national security reporter, wrote an article referencing the top ten viruses. Weinberger’s lists included the Love Letter/I Love You as one of the most destructive viruses (Weinberger, 2012).
Love Letter/I Love You
In 2000, a cybercriminal distributed emails with an attachment labeled “I Love You.” Those that opened the email and launched the attachment received a surprise. The file contained a virus that overwrote image files along with using the Windows address book to forward the email to the first 50 email addresses (Weinberger, 2012). Viruses that use email as a means to spread cause mail servers to overrun with requests and render them useless. In 2000, Bill May, a reporter for The Journal Record, reported that the Federal Aviation Administration’s (FAA) Mike Monroney had shut down its email servers after a virus infected the server and worked to restore files lost from a back-up source (May, 2000).

