Advanced Persistent Threat

Advanced Persistent Threat
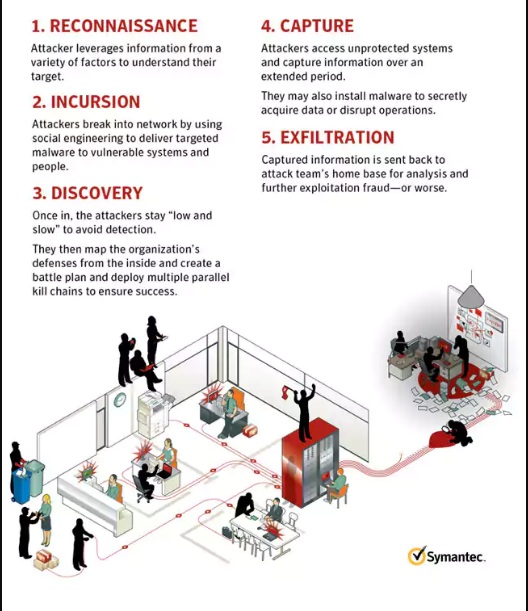
Organizations are under constant attack no matter how large their companies are. Attackers indiscriminately target organizations as large as Governments to as small as Internet start-ups using a method known as the Advanced Persistent Threat method (APT). The APT method utilizes sophisticated, covert attacks bent on secretly stealing valuable data from targeted and unsuspecting companies. It differs from other types of attacks because it focuses on infiltrating a business or companies network and remaining in the system in order to ex-filtrate information. This differs from other types of attacks that focus on getting in and out of a system as quickly and quietly as possible. Advance Persistent Threat is a targeted attack that uses widely known techniques such as malware injection, spyware, or phishing attacks to gain access to a company’s network. The targeted attacks are customized and tailored for the specific targets with the intentions of maintaining a consistent presence in the company’s network. This is a moremeticulous and precise approach than would normally be taken by attackers who are trying to simply access a network, gather information, and ex-filtrate information. APT wants to remain in the system until it completes the specified purpose of the attack. APT wants to remain “low and slow.” APT attacks, as defined by Symantec, are separated into 4 phases. The first phase is Incursion, where the attacker uses various methods to break into a network. The second phase is Discovery, where the attackers learn the vulnerabilities and network of the company in order to better determine which attack vector to exploit. The third phase is Capture, in which the attacker accesses unprotected systems, gathers information, andinstalls malware or disrupts service. The fourth and final stage is Ex-filtration, where the pertinent information that has been garnered is transported out of the system.
Advanced Persistent Threat (ATP)
Phase 1: Incursion
The first phase of the APT method is incursion where an attacker uses wellknown infiltration techniques to gain access to a network. The method meticulously investigates the network in order to derive specific attack vectors. During this step several specific tasks are performed: reconnaissance, social engineering, zero day vulnerabilities, and manual operations.
Phase 2: Discovery
The discovery phase occurs immediately after the hackers have exploited the various attack vectors previously discussed. It is at this point that the hackers gather sensitive information about the company to ex-filtrate. In this stage, the attacker maps out
systems, extracts confidential information, and determines operational instructions and functionality. They may also escalate privileges in order to learn more about the information that is present. The key aspect during this stage is that there is an attack on multiple vectors. The attack is designed to remain in a system for an extended amount of time. During this stage the approach wants to perform considerable analysis and research of the network and its vulnerabilities Once the incursion phase is completed and a beachhead is established, the APT method will attack as many vectors as possible. It will determine if there are anyvulnerabilities with which it can gain a stronghold of the network. After the vulnerabilities are exposed additional software will be downloaded depending on the knowledge gained from the investigated network. The additional software will remain in the system for as long as possible in order to determine as much information about the system as it can. The process is not designed to be quick, but a thorough probe of the system.
Phase 3: Capture
The capture stage occurs once all of the information has been scouted and discovered. The files that are deemed necessary to be ex-filtrated are now collected. TheAPT method will log information over an extended amount of time to collect all the necessary information. The attack can remain in the system for several months, even years, copying and storing date before it is securely moved. Some attackers go even further and design a more active assault rather than a reconnaissance of information. There have been cases of APT attacks that take over and shut down key aspects of companies.
Phase 4: Ex-Filtration
Ex-filtration is the final phase of the APT method where intruders have seized control of targeted systems. At this point they may proceed with extraction of intellectual property or other data. The information can be transported in several different distinct manners such as clear text or encrypted zipped files. The method allows the hacker to work in a distinct level of anonymity; therefore, they have ascertained how to properly move a significantly large amount of data outside of the network without being detected. The knowledge of the network gives the hacker the ability to determine what information it can feasibly move without triggering an alarm. The ability to ex-filtrate without alarming the company will give the hacker an ability to maintain a presence in a system even after they have completed the initial task.

