Experimental And Theoretical Modeling Of Dnp3 Attacks In Smart Grids
Security challenges have emerged in recent years facing smart-grids in the energy sector. Threats are arising every day that could cause great scale of damages in critical infrastructure. Chapter 3 will address the internal security threats associated with smart grid in a simulated virtual environment incorporating DNP3 protocol. We will analyze vulnerabilities and perform penetration testing involving Man-in-the-middle (MITM) type of attacks. Ultimately, by utilizing theoretical modeling of smart-grid attacks using game theory, we can optimize our detection and mitigation procedures to reduce cyber threats in DNP3 environment. The use of intrusion detection system will be necessary to identify attackers targeting different part of the smart grid infrastructure. Mitigation techniques will ensure a healthy check of the network. Performing DNP3 security attacks, detections, preventions and counter measures will be our goals to achieve in this chapter.
Introduction
As we have learned from the previous chapters, Physical and cyber security are using both physical and cyber components integrated with both legacy systems and new technologies running over TCP/IP platform. Legacy Supervisory Control and Data Acquisition (SCADA) systems were initially designed to be isolated systems that had dedicated and separate communication links and therefore cyber or physical security was never considered to be a threat. Today’s systems demand a much higher level of communication to be available in systems involving smart-grid automation components like Intelligent Electronic Devices (IED’s). IEDs are designed to automate protection, control, monitoring and metering for the smart grid system in both peer-to-peer and client server implementation.
SCADA is using several standards and protocols developed over the years to provide communication including MODBUS, DNP3 and latest IEC 61850. Distributed Network Protocol or DNP3, as our main focus in this research chapter, is an IEEE-1815 standard and the primary protocol being deployed in smart-grids system and other utility providers and it is considered to be the predominant SCADA protocol in the US energy sector.
Our current chapter will have three primary goals to achieve:
Review security threats in DNP3 based smart-grid infrastructures and perform MITM attack experiments to show vulnerabilities in DNP3 implementation using Opendnp3 platform as a prototype environment.
Use “Game Theory” to model man-in-the-middle (MITM) attack on DNP3 environment, analyze detection strategies, mitigations and perform Nash Equilibrium analysis.
We introduce pass and drop mitigation technique to reduce the impact of MITM attacks along with the selection of retransmission timer.
In the next sections, we will discuss security threats and attacks facing DNP3 protocol in smartgrid implementations.
Security Threats in DNP3
Security, especially data integrity in communication protocols is one of the most challenging research area involving smart grids. Communication is not just about data transfer, it is about ensuring accuracy, integrity and confidentiality to critical data. Smart-grids are complex environments that facilitate an improved and an efficient two-way path of communication and power handling capabilities. This involves up to date technologies in areas such as power, communication, and renewable energy resources in order to achieve highly secure, reliable, economic, and environmentally friendly electric power system. With increased smartgrid complexity, experimental studies of large-scale grids are usually not economically feasible.
Even for small micro-grid environment with limited number of distributed energy sources and intelligent loads, there are only a handful test platforms around the world. Therefore, simulation, virtualization and theoretical modeling become powerful and convenient tools in this research area.
DNP3 is a reliable and efficient protocol used in the delivery of measurement data from an outstation or slave located in the field to a utility master operating in the control center. Control requests are made from the master to outstations by an operator or using an automated process in addition to time synchronization, file transfer and other related tasks and therefore, it is very critical to study its behavior and application in real-time implementation. According to, many deficiencies and vulnerabilities have been identified in DNP3 including 28 generic attacks. Related SCADA attacks were also studied using techniques including fault trees, attack trees and risk analysis that provide more theoretical approach as opposed to our method that is more specific to DNP3 and based on a combination of experimental and theoretical techniques to complement the conceptual analysis.
Our approach consists of performing three primary tasks starting with identification and testing of potential vulnerabilities associated with smart grid implementations involving DNP3. We will use smart-grid testbed experiments on virtualization environments to analyze vulnerabilities and performing penetration testing using man-in-the-middle (MITM) type of attacks to identify possible threats associated with smart grid. By utilizing theoretical modeling of smart-grid attacks using game theory, we can analyze the outcomes of MITM for DNP3 environment. Ultimately the use of intrusion detection system (IDS) will be necessary to identify attackers targeting different part of the smart grid infrastructure and mitigation strategies will ensure a healthy check of the network.
DNP3 is an open standard that can be deployed using several topologies including point-to-point (one master and one outstation or slave), multi-drop topology (one or multiple masters and multiple outstations) or using the hierarchical layout where systems are arranged in a tree like setup and one outstation could act as both a slave to a DNP3 master or a master to other outstations. DNP3 messages can be mapped to the upper layers of the OSI model and are based on three layers including data link, transport and application layers.
The DNP3 data link frame consists of a fixed size 10 bytes long header block, block 0, followed by 282 byte long data portion divided into 16 bytes blocks and each block ends with two bytes as CRC code. The header is split into a two bytes “sync” field for synchronizing the receiver and the transmitter, a one byte length field that specifies the number of bytes in the remaining fields (with the exception of the CRC length), a one byte control field, two bytes each for source and destination addressing, and finally a two bytes CRC field.
DNP3 Attack Model
In this section, we will simulate an experiment of smart grid environment involving one master and one outstation or slave (Fig. 3.1) for the purpose of investigating important vulnerabilities and possible attack scenarios using MITM.
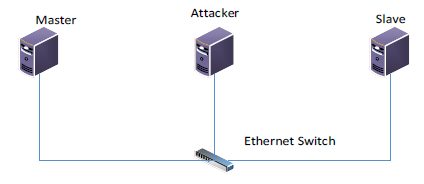
Figure 1 A cyber-attack Model
To set up the infrastructure for performing MITM attack, , three Linux nodes are used to run in a virtualization environment and the following state transition diagram (Figure 2) represents an attack scenario to stop unsolicited messages from the slave in the form of packet intercepting and packet injection.
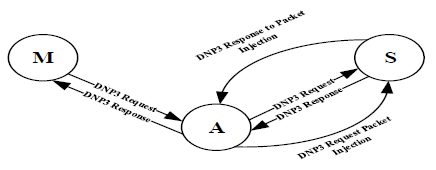
Figure 2 MITM Attack State Diagram 1
The Master (M) and the Outstation or Slave (S) are both running Ubuntu operating system with OpenDNP3 protocol and exchanging dnp3 request and response packets. The attacker node (A) also is running Ubuntu with Ettercap tools and it is configured to be in the middle of the communication between the master and the outstation. Now, to alter the exchanged packets between the master and the outstation, etterfilter was used to enable swift packet modification. The filter was able to capture only the dnp3 packets and Wireshark was used to validate this process.
Attack Setup and Types
To intercept the DNP3 packets, our first step would be to poison the Slave and Master node’s ARP cache by adding the target list for performing the ARP poisoning. Four possible attack scenarios are implemented as follows:
1. Sniffing Slave and Master Generated Traffic:
For sniffing or capturing the traffic passing between the master and the slave nodes by the attacker, Ettercap was used to perform the attack by adding both master and slave IP to the target list, and then ARP poisoning was initiated, and sniffing option was selected. Now in order to push all the traffic passing through the attacking node to our source code, we use the “nfqueue” python module in combination with Linux “iptables” utility that can be used to allow or to block incoming or outgoing traffic on specific ports.
2. Selective DNP3 Packets Dropping Attack:
Now, the Attacker node can view the DNP3 traffic of both victims and in order to drop the traffic generated by any of them, an Ettercap filter is created to specify the conditions to enable selective dnp3 dropping.
3. DNP3 Packets Modification Attack:
In order to modify the content of a specific DNP3 payload, the filter is modified and the payload is replaced with a new one. Here the attacker tries to manipulate DNP3 packets by imposing changes to the exchanged packets. Actually the attacker will capture one of the exchanged packets from the source to the destination and will apply modification to the DNP3 payload in order to portray different message to the destination while maintaining the proper sequence and acknowledgment numbering (SN) and (AN) and performing the new CRC and other packet adjustments, thus preventing the system from detecting such an attack.
4. DNP3 Packet Injection Attack:
To inject a new DNP3 packet into the traffic stream, the filter is modified and the attacker keeps track of the exchanged traffic between the dnp3 stations and monitors the sequence and the acknowledgement numbers and make the move to inject a totally new packet with newly predicted SN and AN. Also, the attacker will maintain a response to the injected packet and make sure it is dropped. Attacker, then will stop the MITM attack and the communication resumes between the master and the slave. Both scenarios, 3 and 4 can result in a major impact to the smart-grid network based on the intended message modification used by the attacker.
Manipulating DNP3 traffic
To manipulate the dnp3 traffic, we created a code to capture a packet instance and to check the length of the TCP before modification and replace the contents of the payload with the modified one and get the new length of the TCP packet, payload and compute the difference in length between the new and the old and set the new IP length field, delete both of the IP and TCP checksum fields so the scapy would recalculate this and finally accept and forward modified packet.
In order to send the modified packet, a new TCP session was initiated with the slave node listening at the dnp3 port 20000, and another hijacking technique was invoked to take over the existing TCP session. The test results showed that the attacker; by modifying the TCP/IP header and DNP3 messages, was able to manipulate, control and redirect the DNP3 traffic and even change the exchanged messages (DNP3 payload) between the master station and the outstation.
Unsolicited messages Attack Example
Unsolicited messages is considered to be a way the remote terminal unit (RTU), or the outstation, can communicate certain activities or events data to the master station without being polled. Messages can be in the form of specific readings, warnings, or errors detected by the outstation that need to be sent to the master station for further and immediate actions. It is a way to ensure that current status is understood by the master station, for example unsolicited message from the RTU in a smart-grid environment can be sent to the master to indicate that the load’s requirement has decreased and it needs to be changed by the master station to a different value and the outstation will be expecting to receive the control message from the master.
In virtualization environment while normal communication is occurring between the master station and the outstation exchanging DNP3 messages encapsulated in TCP/IP packets, an attack is successfully performed to intercept the communication by stopping the outstation from sending unsolicited messages without impacting the normal communication behavior. Such an attack can lead to very disastrous situation if such penetration occurred in the smart grid network. Figure 3
shows an example of security penetration executed by the attacker to intercept the communication channel and to inject the malicious payload data without impacting the rest of the communication session.

Figure 3 A cyber-attack scenario – DNP3 Unsolicited Message Attack
