Espionage in Action
a.Chaos Communication Camp
At Chaos Communication Camp, in 2015, organizers distributed rad1o badges, shown in Figure 1. These devices are approximately the same size as a Raspberry Pi and include an antenna, allowing the user to intercept traffic on the Iridium satellite network. As is, they were able to intercept approximately 20% of the pager traffic on the network due to the cheap antenna that was used. With a proper antenna the interception rate could be increased to 100%. “The problem isn’t that Iridium has poor security. It’s that is has no security.” After this camp, additional work has been done to intercept other types of traffic on the network utilizing the same device. Technologies like this have advanced so rapidly that in 2008 Iridium stated that “the complexity of the Iridium air interface makes the challenge of developing an Iridium L-Band monitoring device very difficult and probably beyond the reach of all but the most determined of adversaries.” Following the ending of the camp the organizer mentioned that “It’s kind of a myth that satellite hacking is hard.”
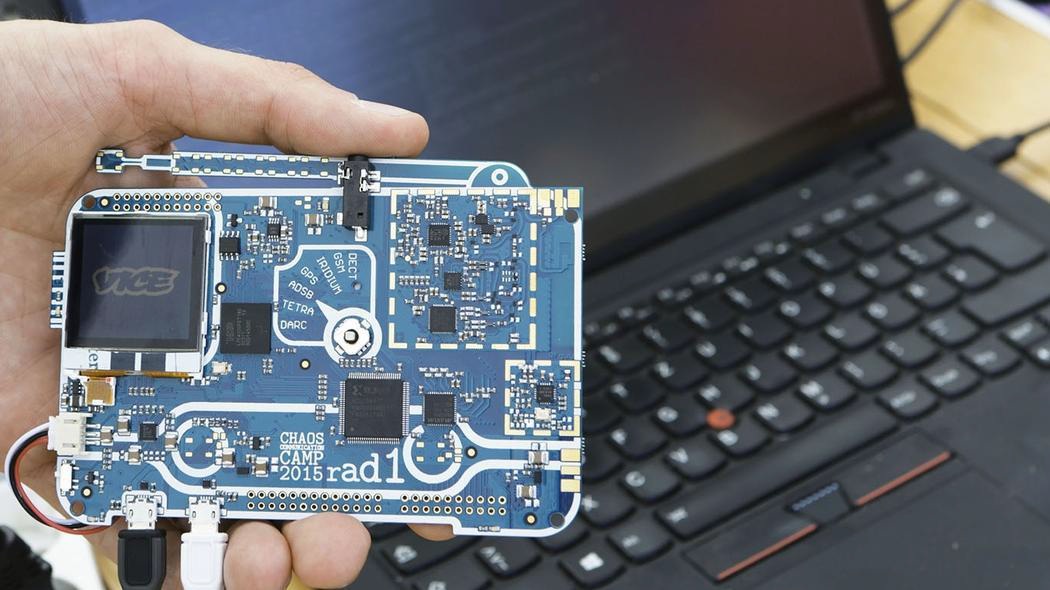
Figure 1 – Rad1o Badge
b.SATCOM
IOActive in Seattle, Washington, performed an analysis of the security on Satellite Communications (SATCOM) and published a comprehensive study in 2014. This analysis utilized publically available firmware to search for vulnerabilities, and in many cases did not even require the physical device to find vulnerabilities. Types of vulnerabilities found included poor protocols, backdoors, and hardcoded credentials allowing attackers to modify communications and even take control of the device. A single compromised device has the potential to expose other portions of the SATCOM infrastructure and affect all customers. “The findings of IOActive’s research should serve as an initial wake-up call for both the vendors and users of the current generation of SATCOM technology.” According to Santamarta, “encryption use isn’t as common as it should be. SATCOM services are expensive and data charges are a major drawback when introducing secure communications.”
c.Turla Advanced Persistent Threat
“Turla is a sophisticated Russian cyber-espionage group, believed to be sponsored by the Russian government that has targeted a number of government, military, embassy, research, and pharmaceutical organizations in more than 45 countries including China, Vietnam, and the United States.” These hackers have been able to exploit older satellites that do not support encrypted connections. Due to the large broadcast area, they can operate anywhere within it to effectively mask the true location. Once a satellite is in range, the attackers can monitor the traffic and attack other users of the same service. A diagram of this process is shown below in Figure 2.

Figure 2 – Turla APT Scheme
d.NASA / NOAA
To give some examples of the vulnerability of satellite systems, a draft report of the US Congress in 2011 recorded that at least two US environment-monitoring satellites has suffered interference four or more times in 2007 and 2008. A Landsat-7 Earth observation satellite build by NASA and managed by the US Geological Survey experienced 12 or more minutes of interference in October 2007 and July 2008. A NASA-managed Terra AM-1 Earth observation satellite suffered similar interference for two minutes or more on a single day in June 2008, and at least nine minutes on one day in October 2008. The US National Oceanographic and Atmospheric Administration (NOAA) reported that its Satellite Data Information System was taken offline in September 2014 after a serious hacking incident; this denied high volumes of data to weather forecasting agencies around the world for 48 hours.

