Encryption Functionalities
When discussing encryption functionalities, Skular (2009) stated, “The primary solutions needed to protect data on a mobile computer [devices] are encryption as well as “remote kill” capabilities” (Skuler, 2009, para. 6). For the purpose of this paper, which examines the various factors of data encryption, the author will not go into further details on the protection feature of “remote kill” as referenced by Skuler. Perhaps, this discussion could fall in the category of future research.
Today’s cryptosystems are divided into two categories: symmetric and asymmetric. Symmetric crypto systems use the same key (the secret key) to encrypt and decrypt a message, and asymmetric cryptosystems use one key (the public key) to encrypt a message and a different key (the private key) to decrypt it and all of today’s algorithms fit within those two categories. (SANS Institute, 2001, p. 7).
In the following section the author will discuss the unique characteristics of the two commonly used encryption cryptosystems to build a generalized understanding of its usages in message and/or data (e.g., audio, text, and video) encryption and decryption. There are numerous cryptographic encryption algorithms that are used to protection information from unintended disclosure—to ensure that the content of the communication is viewable only to authorized recipients. Some of the common available algorithms include “AES [Advanced Encryption Standard] (Rijndael), DES [Data Encryption Standard], 3DES [Triple-DES], RC2, Blowfish, and RC6” (Elminaam, Kader, & Hadhoud, 2010, p. 1), which falls under to the two encryption cryptosystems known as: Symmetric and Asymmetric. Although, this paper discusses the encryption cryptosystems, it is not the aim of the author to capture the technical descriptions of the various encryption algorithms (e.g., DES, AES, Blowfish, and RC2) in detail. “Encryption is the most effective way to achieve data security” (Lites, Allday, & Fife, 2015, p. 2). To read an encrypted file, you must have access to a secret key or password that enables you to decrypt it” (Lites, Allday, & Fife, 2015, p. 2). Refer to Figure 3 for a general description of the basic operations of cryptographic encryption process (Lites, Allday, & Fife, 2015, p. 1).
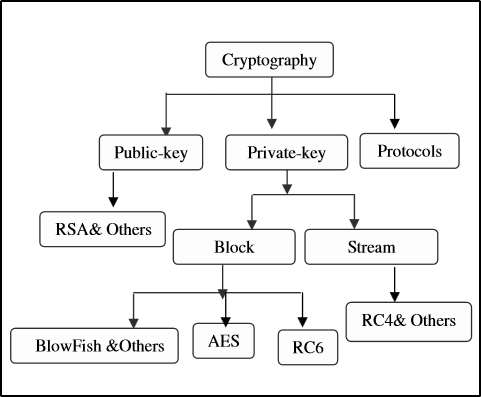
Figure 3: Common Cryptographic Encryption Techniques
Source: http://isrc.ccs.asia.edu.tw/ijns/contents/ijns-v10-n3/ijns-2010-v10-n3-p213-219.pdf
Symmetric Key Encryption
As stated earlier, “symmetric keys encryption or secret key encryption, only one key is used to encrypt and decrypt data” (Elminaam, Kader, & Hadhoud, 2010, p. 1). In this method of encryption the cryptosystem shares one secret key between the an originator and a recipient of the communications medium for message encryption as well as decryption (Linn, 1993, p. 7), which lacks security, if the key is intercepted, loss, and/or stolen—making this encryption cryptosystem algorithm more vulnerable compared to its counterpart (i.e., asymmetric).
Asymmetric Key Encryption
“In Asymmetric keys, two keys are used; private and public keys. Public key is used for encryption and private key is used for decryption” (Elminaam,Kader, & Hadhoud, 2010, p. 1). According to O’Connor (2014), “Asymmetric systems are also called public key cryptosystems, and are the basis of RSA techniques, of which PGP (Pretty Good Privacy) is the most well-known implementation” (ENCRYTPION, para. 3). This form of encryption cryptosystem is a two-prong encryption and decryption process. For instance, the author of the communications medium will use a public key to encrypt the communications medium and sends the private key to the intended recipient to apply the decryption process—reviewing the ciphertext, cipher audio, and/or cipher video in plaintext view or legible form (human-readable).
“The use of two keys overcomes a major weakness in symmetric key cryptography, since a single key does not need to be securely managed among multiple users” (Lites, Allday, & Fife, 2015, p. 8). Based on the above analysis of the two encryption cryptosystem algorithms, asymmetric appears to be a more secure and preferred method for communications encryption and decryption. (Lites, Allday, & Fife, 2015, p. 12) provided the following illustration of a sample substitution cipher usage, which is depicted in Figure 4.

Figure 4: Sample Cipher Text
Source: http://peace.saumag.edu/faculty/kardas/Courses/CS/Encryption2015.pdf

