Data Encryption
encryption offers end users a sense of security regarding the protection of sensitive data and/or information—providing defensive cyber strategies against data breach, data exfiltration, and network exploitation through an array of cyber intrusion threat landscapes (e.g., viruses, malware, spearphishing, and MitH) from unauthorized users such as hackers, cybercriminals, and the likes. “Mobile devices can be used by a hacker as an access point into many other aspects of your digital life as well the lives of others in your network, making mobile security about more than just protecting your phone” (Certic, 2013, p. 2). Mobile users need education and awareness regarding such potential cyber intrusion threat landscapes that cause security, data exfiltration and/or network infection concerns.
Security gaps on mobile device can also enable cybercriminals to leverage the use of infected mobile devices as gateways to conduct further CNE opportunities against targeted victims on the same network and/or cross-network penetration. Certic (2013) stated: A recent common hacking method works by forwarding the network traffic sent by the control server to another host in the network, which could be any other device inside a corporate network if the mobile device is connected to an internal Wi-Fi. Essentially, if you fall victim to this, you are exposing attackers to your entire digital life as well as that of anyone connected to your network.
“Some of the most prevalent mobile viruses and worms use an unprotected Bluetooth connection to get into mobile devices or to spread to other devices. This includes two of the most common mobile device viruses, both with a number of variants, Cabir and CommWarrior” (Bancroft, 2008, para. 13). Additionally, mobile devices on home networks connected via Wi-Fi are just as susceptible to similar cyber threat landscape attacks as Certic had put in the limelight. Certic (2013) also mentioned that modern mobile phone connectivity has transcended the standard Global System for Mobile Communications (GSM) and Code Division Multiple Access (CDMA) cellular service connections—in which network connectivity such as 3G, 4G, LAN and WLAN connection capabilities are ubiquitous in modern societies—enhancing the convenience and adaptability for mobile users. Couture (2010) stated “One of the challenges of mobile device security are the numerous types of connectivity available on a current generation smartphone.
The attack surface is broad and encompasses a trove of possible attack vectors” (p. 12). According to Sacco (2007), “Forty percent of respondents access the Web via an open, or unsecured Wi-Fi connection in any given month, be it public or another person’s personal network” (para. 2). The expansion of modern day network connectivity interfaces on mobile devices have afforded mobile users the flexibility and capability to connect to the Internet at random via mobile-enabled networks (e.g., AT&T, Verizon, and Sprint), and through Wi-Fi connections, which are most commonly found at Internet or Cyber Cafes, Hotspots, Airports, and so on. Nowadays, mobile users are able to share photos, documents, and other personal information with friends and family members through SMS, WeChat, Twitter, Facebook, and a wide range of other online Web 2.0 applications—putting their whole life story in the virtual world.
Additionally, mobile users are able leverage the Internet to make online transactions such as banking, credit card applications, mortgage applications, bill payments, movie ordering through mobile applications like Fandango, loan applications, and other online purchases (e.g., Amazon, eBay, and Apple Store). It appears that for the average mobile user, the virtual world is just as
important—almost everything that associates with the individual’s life (e.g., social networking, school, work, friends and family members; banking and finance; and entertainment) in modern societies are interconnected with the virtual world (i.e., Internet)—readily accessible in the palm of their hands (i.e.. mobile devices).
According to Couture (2010), the hackers’ motivation and inspiration to conduct CNE activities for financial gain on mobile platform devices were largely non-existent; however, that is not to say that with the robust architecture and processing powers on mobile devices, this trend could likely redirect hackers’ motivations to target mobile devices, especially for devices that are
interconnected with corporate networks, government sectors, academia, etc.As the idiom goes, “necessity is the mother of invention” and so far, there hasn’t been a strong need to exploit mobile devices for use in botnets of for the personal or corporate information stored within. With the significant increase of data speeds and always-on connectivity, the former [cyber-attacks against traditional operating system platforms, Adobe Acrobat applications, FLASH, and Microsoft Office products] becomes more palatable as a means to leverage the world’s hundreds of millions of mobile devices to send spam or launch denial of service attacks. The latter leaves to be proven, but as users entrust more and more valuable data to their phones, they can only become more desirable a target to cyber criminals. (Couture, 2010, p. 6)
Statistic Brain Research Institute (2015) conducted on survey with mobile users regarding the practical applications, types of data usage, and mobile technology integration to introduce the average statistics on mobile device usages, a research study that was completed by Qualcomm. Refer to Figure 1 for detailed descriptions on mobile device usages.
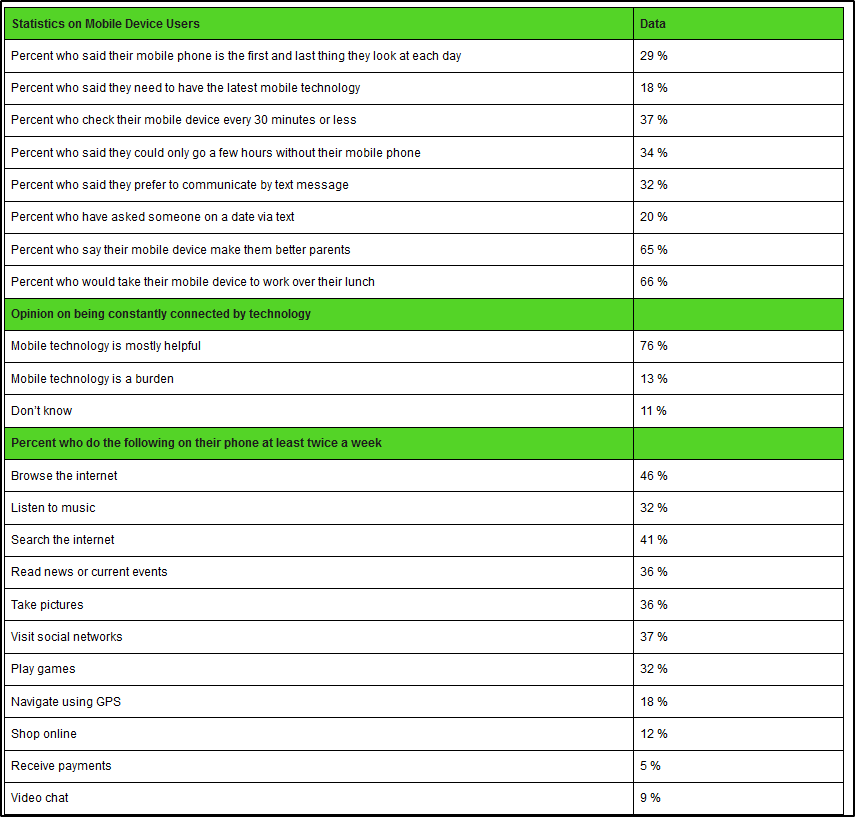
Figure 1: Mobile Device Statistics
Source: http://www.statisticbrain.com/mobile-device-cell-phone-statistics/
Bosomworth (2015) illustrated a separate comparative analysis research study conducted by Morgan Stanley Research on obile device usage, depicts the constant rise of mobile device usage overtaking desktop computers in an 8 year span (from 2007 to 2015). The numbers are staggering and gaining historical ground. By mid-2014, mobile device users worldwide have surpassed desktop users, which jump from approximately 400 million users in 2007 to nearly 1,700 million (1.7 billion) mobile users by 2014, and it is still on the rise to reach 2 billion users (by the end of 2015 or early 2016—nearly one quarter of the current world population at 7.3 billion people (De Wulf, 2015). Figure 2 is one of the latest comparative analysis statistics depiction on mobile and desktop users globally.

Figure 2: Number of Global Users
Source: http://www.smartinsights.com/mobile-marketing/mobile-marketing-analytics/mobile-marketing-statistics/
Another research conducted by Pew Research Center on Mobile Connectivity in 2012 stated, “Some 85% of American adults now own a cell phone of some kind, and these devices mean many things to their owners: an always-available link to friends and family, a pocket computer, or a time-saving tool … ” (Smith, 2012, para. 2). Based on the previously noted research, the number of mobile device users have reached to an unprecedented scale—replacing desktop applications by the millions.
According to the natural trend of today’s society, the average mobile user has put their entire livelihood on the Internet by way of network protocols that are widely available in the global arena. Although such technological advances on mobile connections and capabilities have created significant convenience and multi-functionalities for mobile users; however, where this is convenience, there are also security concerns with such technological advances in mobile connectivity. Certic (2013) referenced “One of the ways that mobile devices security can be improved is through two-step authentication system. It consists of a server connected to a GSM enabled service provider and a mobile phone client equipped with SMS receiving functionality” (p. 3), which appears to be a good parameter cyber defense strategy—making it “difficult for hackers is because not only do they need to get your password and your username, but must also gain access of your mobile phone as well” (Certic, 2013, p. 3).
But what happens when the parameter defense mechanisms fail and the hacker or cybercriminal has already gained access to
the mobile device? How is the data protected against exfiltration, manipulation, destruction, and/or modification? On a separate note, Couture (2010) claimed, “The number one unique threat to mobile computing it physical loss or theft of the device” (p. 7). In this scenario traditional parameter defense mechanisms (e.g., password-protection, anti-theft protection, firewalls, and antivirus software) will not be effective against the physical loss and theft of mobile devices.
According to a survey commissioned by Pointsec, 85,000 mobile phones and 21,000 PDAs and smartphones were left on taxis in Chicago over a 6-month period in 2007. The survey also found that more than 63,000 mobile phones and 5,800 PDAs and smartphones were left in London taxis during the same 6-month period. (Bancroft, 2008, para. 5). Based on these findings, data encryption is a prudent process that mobile users need to implement. The power of data encryption will be more effective against data exfiltration.

Data Encryption

