The Current State of Cyber Security in Industrial Control Systems
The primary objective of Enterprise Information Technology (IT) is for the movement, storage and protection of all data. The data may be records or logs that are commercial or personal in nature, intellectual property or confidential communications. The industrial sector uses technology similar to IT which may be specifically built for manufacturing products and materials, moving people or controlling and supervising utilities. This is referred to as Operational Technology (OT) specifically designed to for viewing, controlling and supervising “devices in motion”. In comparison to enterprise IT systems, the security of OT systems is concept that is relatively immature. Apprehensions with OT security has existed for decades, however new interest in security and resilience of infrastructures has been heightened since the September 11 attacks and the Stuxnet worm attack in 2010 . Since its inception Industrial Control Systems have exploited proprietary communication protocols and hard ware which is used to interface operators and engineering workstations with control processors. These protocols and networks were designed with a trust model that was implied. This concept assumes that components will only communicate information that is
formatted truthful, properly formatted for individual consumers and does not require authentication. There has been a recent shift to using network technologies such as the TCP/IP protocol stack and Ethernet. These technologies enhances the ability to install and maintain the system while reducing costs. It however makes the system susceptible to vulnerabilities that are in these well-researched and popular technologies. Legacy control systems however still use protocols that are inherently insecure such as FTP, Telnet, Object Linking and Embedding for Process Control (OPC) as well as DCOM/RPC. Many owners of ICS assets still believe in the myth that their primary line of defense should be an “air gap” that separates the enterprise IT network from the industrial control network OT. That myth has been analysed and refuted as a means of securing the OT network . There are numerous ways by which air gaps can be violated namely: network bridges used by employees that are undocumented, remote maintenance by vendors and laptop computers which are connected to the network intermittently, USB transfers, DVDs and CDs are threat vectors that break the air gap myth. Malicious attackers are often not required to become overly creative to access numerous industrial control systems as a large number of industrial components are already connected to the internet directly. Thousands of devices communicating over standard ICS protocols can be revealed by using an internet search engine called SHODAN (www.shodan.io).
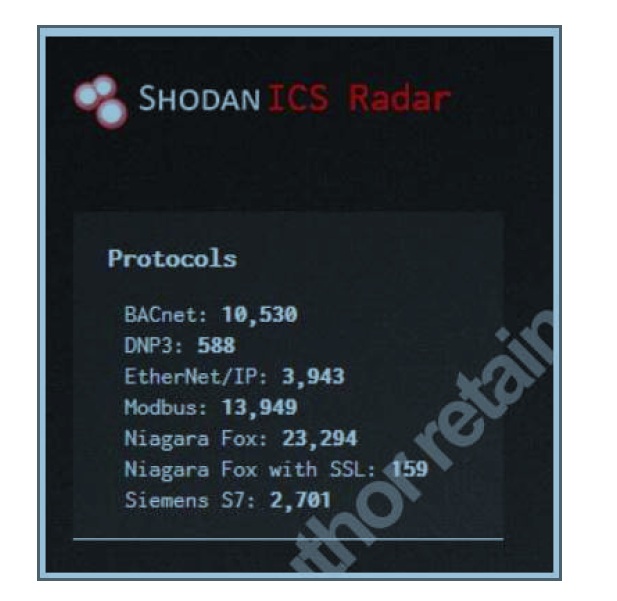
Figure 1. Shodan Radar Output of devices based on ICS Protocols

Figure 2. Shodan Diggity – Provides an easy to use, free scanning interface for the SHODAN
Openly available search tools such as SHODAN highlights the fact that there exists a lack of understanding when designing ICS systems. For instance if an ICS network was installed next to an IT enterprise system. In order to carry out system maintenance, engineers created an unauthorized bridge between the networks due to a legitimate maintenance need. A comprehensive network design would account for the valid instances where there is a need to have network segmentation and security controls. The air-gap myth must be abandoned in the interest of advancing ICS security. Owners of ICSs must embrace the concept of an interconnected production plant floor which facilitates traditional security safeguards such as security patches, antivirus, software updates, as well as Intrusion Detection alert rules. SCADA and ICS architectures must be designed and implemented with these inherent security features.

