Cryptographic Principles
“Confidentiality is defined as the assurance that information is not disclosed to unauthorized entities or processes.” As spacecraft require a radio frequency (RF) space link, the only means to achieve confidentiality is through encryption. Encryption allows only the initiator to transform ordinary data, plaintext, into unintelligible data, ciphertext, for safe transmission to the recipient. The sender and receiver share a secret key that makes the reverse of this process, decryption, possible. Encryption eliminates the threat of a third party interpreting the data. Integrity of data can be summarized as accuracy. Is the data received the same as what was sent? Many threats can be eliminated with proper error checking and verification. The issue of integrity in space link communications has always been considered due to environmental factors and noise on RF links. One method of validating integrity is the use of a cryptographic hash function. A hash function is a one-way process that generates a fixed-size hash value for a variably sized input. This is nonreversible, unlike a cyclical redundancy check (CRC), and responds to any minor modifications with a different hash value. An example of this can be seen in Figure 1. It is infeasible that two messages with the same hash value will be generated.
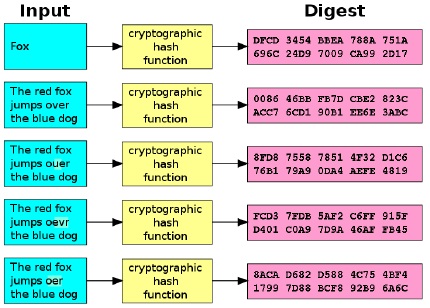
Figure 1 – Cryptographic Hash Example
“Authentication can be used to uniquely identify a person or entity.” This allows access control to be implemented, as well as the logging of activities for traceability. “Authentication is implemented by either hash-based or cipher-based message authentication codes. It can also be implemented by use of digital signatures.” A Message Authentication Code (MAC) is utilized in the Space Data Link Security (SDLS) Protocol discussed in Section 2.5.4. This MAC is similar to a hash, except a secret key is needed to generate the MAC. This MAC also guarantees that the message has not been altered. A depiction of the entire process, sender to receiver, is provided in Figure 2.
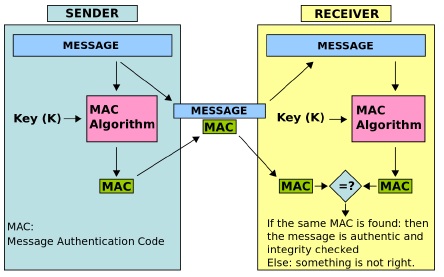
Figure 2 – Message Authentication Code Diagram
Availability is the most difficult cryptographic principle to obtain on a spacecraft. In software, all that may be done is ensuring that messages are received in sequential order and that requests for retransmission are performed. Additionally, bounds for certain values must be checked quickly, as that packet may be ignored so that others can be processed. Examples of what drives this need are captured in the next section.
Threat and Risk
Threat and risk are defined before the types of attacks currently known to the space industry are discussed, along with the risk this places upon the spacecraft and the owners. A deep dive into CCSDS protocols in use for this work follows in Section 2.5. These protocols are layered and broken down from the top level implemented and address the issues captured in this section.
“A ‘threat’ is a function of a threat agent’s capability and intent to do harm whereas ‘risk’ is a function of the probability that an organization will be targeted and the harm that might be caused. To further distinguish the difference:
Threat = Capability x Intent;
Risk = Probability x Harm.”
With the commercialization of space and the growing number of satellites in orbit, the number of threats and amount of risk are increasing as well. As new capabilities in space become available, the risk increases and further drives interest in security. A large number of spacecraft, including large missions, do not have any type of security, further emphasizing the need for this protocol and additional work in the realm of security in the space industry. “In the past, space missions using CCSDS Recommended Standards were typically thought of as ‘civil’ and ‘scientific’ missions that were not likely targets of malicious attackers, unlike military missions that would be targeted and have traditionally been highly protected.” A number of these recent attacks are detailed in Section 2.4, but understanding the threats is vital in determining the amount of risk. “A threat agent (or threat source) can be human or non-human and can be intentional or unintentional.” This section will detail potential types of threats to space systems. These threats originate from multiple sources. Each component or piece used on a mission has the potential to contain threats against it specifically. Some of these are captured in Figure 3 below.

Figure 3 – Generic Threats to Spacecraft
