Combined Cyber-physical attacks
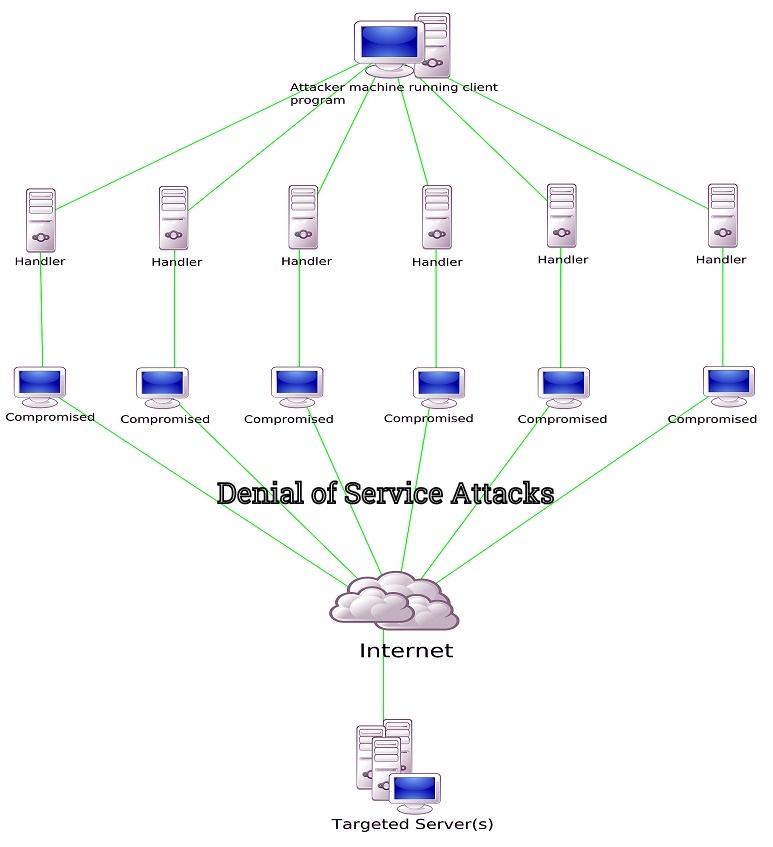
Denial of service attacks
Addressing the issue of combined cyber-physical on the grid attacks is an ongoing effort in between the private and public sectors. Cyber-physical attacks, also known as blended attacks, are executed by an attacker or by inadvertent activities which have greater impacts or consequences that are different compared to an individual cyber or physical attack. The heightened impacts generated by blended attacks, must be considered when evaluating the risks and vulnerabilities of individual cyber or physical attacks. High-level security requirements must address the impact due to cyber vulnerabilities. The appropriate selection and tailoring of requirements, makes it is possible to address some physical vulnerabilities of the electric power grid. ISA 99 and NIST SP 800-82 Rev. 1, discuss Control System Security, and provide guidelines which help to address cyber physical attacks .There are three categories of cyber-physical attacks:
1. Physical attacks which are informed by cyber – This involves using information which was gathered by cyber methods and enables an attacker to strategize and execute an enhanced physical attack. For example, an adversary decides to destroy the components inside a substation despite not being certain which components or substation will have the most significant impact. If they have access to confidential information or accumulates unprotected information using a cyber means which informs them that a specific substation is on an exceptionally congested path and has electrical conductors operating at their maximum ratings, then the attacker can carry out targeted physical attack on the lines of that specific substation. This type of calculated attack would have a greater impact compared to a random attack on a substation.
2. Cyber-attacks that enhance physical attacks – This type of attack occurs when an attacker uses a cyber method to enhance the effect of physical attacks by making the physical attack even more successful with greater consequences or by interfering with the restoration efforts hence lengthening duration and resulting impact of the attack. Although the term “attacker” is used, inadvertent activities can also result in such an attack. An example is an attacker tampering with settings of protective relays prior to initiating a physical attack on electrical power lines. While the original relay settings were calculated to contain effects posed by a failure, tampering or replacement with new settings will allow the failure to cascade resulting in impacts to a wider segment of the electric grid. Another scenario is the attacker performing a Denial of Service (DoS) attack right after a physical attack. This would compromise the effects of restoration activities and support systems. This type of attacks prolongs the resulting outage.
3. Using cyber systems to trigger physical harm – This mode of attack uses a cyber system which controls physical equipment in such a way that causes physical harm and damage. An instance of this involves the burner management system (BMS) of a natural gas generator. In this scenario, an attacker or a thoughtless operator attempts to turn on the generator natural gas inflow without first ensuring that an ignition source is present. As the burner chamber fills up with natural gas, the attacker would then activate the ignition source, and potentially cause an explosion. Cyber-physical attacks significantly enhance the impact and overall consequences of an attack and can increase dramatically the duration of those negative consequences by interfering with or delaying responses.
These impacts can be minimized by well-designed physical, cyber, and operational security implementation and planning. Defensive measures minimize the likelihood and impacts of a successful cyber, physical or cyber-physical attack. Security operators must consider both individual types of attacks as well as how they could be used together so that improved systems
can be developed that are resilient and mitigate and cyber-physical attack. The effective implementation of NISTIR 7628 along with other security guidelines and standards must be incorporated in an organization-wide process of risk management in order to reduce cyber vulnerabilities and cyber-physical attacks.


