Artifacts of Google Chrome Operating System from SSD Image Capture
AccessData Forensic Toolkit provided an in depth view into the contents of the data stored onto the SSD. It included space for the Unified Extensible Firmware Interface used to replace BIOS in newer systems that handles basic device control to enable booting up anoperating system. The Forensic Toolkit carved out 647 data objects in the image as exhibited in Figure 1.
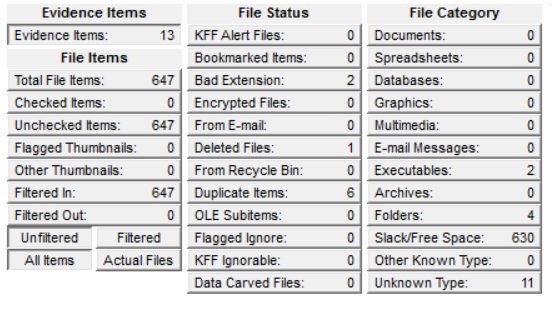
Figure 1. FTK Object table of captured image after carving.
Note the processing carved out 13 areas from the drive space with each consisting of varying contents. Figure 2 shows the labels provided by the file-carving tool culled from the file system objects, and offered a tree view structure of what each of those spaces contained.

Figure 2. Thirteen areas carved from SSD space
Referring to the paper by Fang et al., the three KERN (Kernals), three ROOT (roots A, B and C), RWFW (Read/Write Firmware), and EFI-SYSTEM (UEFI and boot loader) are objects expected in this discovery. Within the EFI-SYSTEM object group, there were 12 contained artifacts. FTK displayed them in tree as shown in Figure 3.

Figure 3. EFI-SYSTEM object group from data carve
AccessData’s Forensic Toolkit revealed the UEFI sector was a FAT16 file system, using Syslinux and Grub for its boot loader as shown in Figure 4.

Figure 4. Grub in boot sector.
Browsing the Hex contents of each of the other twelve carved object groups in FTK revealed that KERN-C, OEM, reserved (10) and reserved (9), ROOT-C, and RWFW each filled with all 00 values. While the others had portions of mixed Hex values revealing binary executables and files that used compression and encryption, these sections were very clearly just unused storage space at the time of the Image capture. These were sections allocated for use, but did not provide useful artifacts. Fang et al. explained how two versions of the operating system were maintained on the system as part of ensuring the system could boot even in the event of a failed operating system upgrade. The objects carved out from the image support that design.
Considering further the paper, it is clear that the User area of the Chromebook SSD artifacts found inside the object group named STATE in Figure 5.

Figure 5. FTK showing User work of SSD Image named STATE
In the early space of this block of the SSD, was some plain text content supporting the view that the STATE part of the drive is the User space as shown in Figure 6.

Figure 6. Start of User space
After completing the manual viewing through all the carved out portions of the Chromebook SSD image, the examiner found no further useful artifacts.
