Artifacts of Google Chrome Browser in Windows XP VM While Logged In
The examiner used up a Windows XP VM with the latest version of the Google Chrome browser installed on it. The approach was to use the VM to log in to the Gmail account and run software to scan for user data to determine what artifacts may exist while logged in. This shall reveal any data produced while a Chromebook connected to an active Gmail account is subsequently stored in Google’s Cloud. It was also to determine artifacts when logged into the account from other devices. This is the first portion of the examination that actually revealed real user data compared later with the manual walkthrough on the Chromebook itself. The examiner used ChromeAnalysis Plus Trial to parse the Chrome artifacts inside the Windows XP VM. Figure 7 and 8 present the user’s Chrome directory contents and the activity using Google Chrome browser functions respectively.
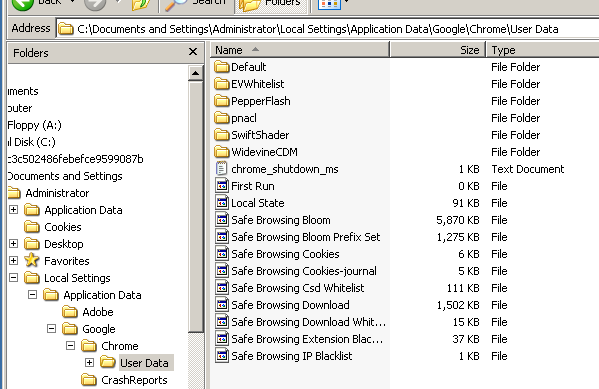
Figure 7. User directory containing Chrome files
 Figure 8. Website History from Google account
Figure 8. Website History from Google account
Google Chrome browser provides the user history so they can quickly find a website they may have forgotten to create a bookmark for returning or else did not make it before realizing they probably should have for later revisit. Note Google Maps, a page of Chromebook backup utility instructions and some YouTube links are included in the listing. As shown in Figure 9,
only a handful of bookmarks were discovered. These bookmarks may be significant to the investigation, as they are clearly sites the user wishes to be able to return to in the future since the user bookmarked them.

Figure 9. Bookmarks stored in Google account.
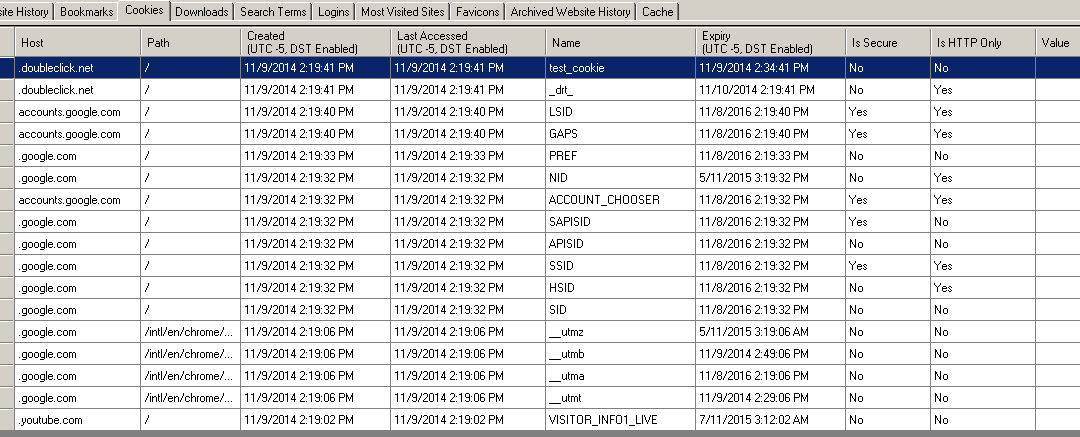
While cookies are less interesting than the Uniform Resource Locator (URL) of websites, advertisements create many kinds of cookies. Some may be useful as they may be part of websites that the user logs into regularly and provide additional information for investigators to collect additional artifacts in support of a forensic investigation. Figure 10 displays many of the
cookies preserved in the Google account used by all browsers logged into the user account. Figure 10. Cookies from Google account.

Figure 10. Cookies from Google account.
Figures 11 shows the download history associated with the local Chrome browser and reveals nothing from the Google account logged into by the examiner. This will be a notable place to look during the manual walkthrough in the next section.

Figure 11. Empty download history from Google Account
Search history is also associated with the local browser install and is thus empty as Figure 12 shows. Note that in the History section, there were Google website searches included. This is also a place to look closely at during the manual walkthrough in the next section.

Figure 12. Empty Search history.
The login history panel is for use of the local browser to reveal a user logging in remotely to server accounts and is empty as shown in Figure 13. This will be looked closer in the manual walkthrough in the next section.

Figure 13. Empty Login History for remote accounts.
The Google Chrome browser notes websites visited frequently and provides some possible insight as to user tendencies. Figure 14 shows the two most visited websites by the user of this Gmail account.

Figure 14. Most visited website list.
These was a listing of the web-icons used for the websites bookmarked in the browser. The data in Figure 15 is notable as a function of the tool used, yet it is of limited forensic value in this investigation.

Figure 15. Icons from websites in favorites (bookmarks).
The user had not locally used the archive function of the Google Chrome browser and Figure 16 shows it empty.

Figure 16. Archived webpages unused.
Figure 17 lists some of the files in the browser cache. This listing is perhaps the most interesting artifacts from the browser. It is also the most densely populated of the types of data that the ChromeAnalysis tool carved out of the local install of the Google Chrome browser. The local directory of the browser cache in this case was:
C:\Documents and Settings\Administrator\Local Settings\Application Data\Google\Chrome\User Data\Default\Cache

Figure 17. First 25 from cache.